Windows Firewall settings can be altered through Control Panel > System and Security > Windows Firewall OR Control Panel > Windows Defender Firewall. The interface call also be accessed through Powershell or Command prompt by entering 'firewall.cpi'
The below is the graphical view of the firewall summary and settings.
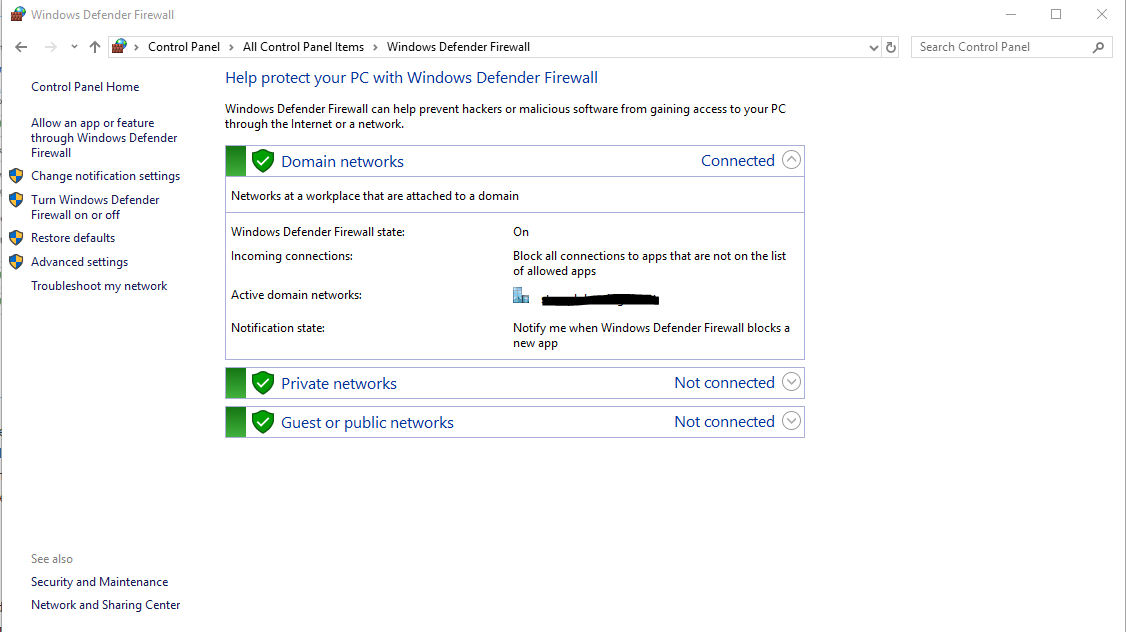
To get to the Advanced firewall settings in the image above you will notice on the left hand side the "Advanced Settings" link. Press this to be taken to the Advanced firewall settings.
You can also get directly here by running 'wf.msc' in either Powershell or Command prompt.
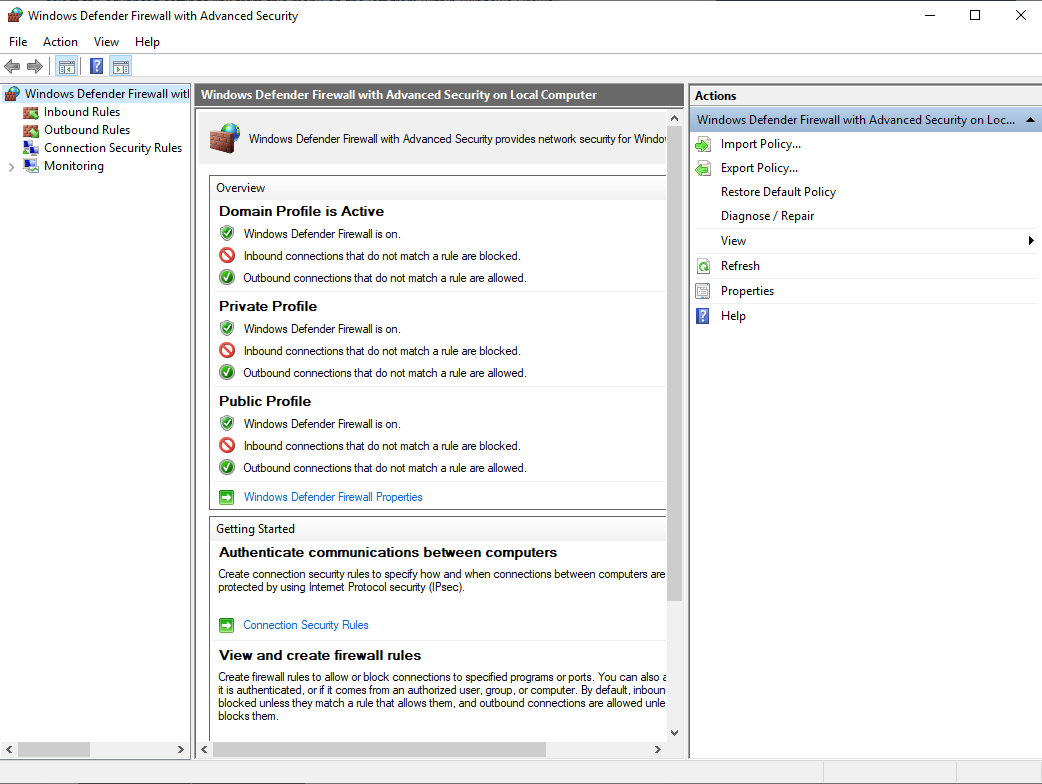
On this window we can see an overview of the domain, private and public profiles, which by default should all be enabled and blocking inbound traffic and allowing outbound traffic.
Under inbound and outbound rules we can view the rules that exist and that are currently enabled. These rules are available by default, rules with a green tick icon on the left are enabled and will allow traffic in while rules with no icon are disabled.
A rule that is disabled can be enabled by simply right clicking it and selecting enable. Likewise we can right click an enabled rule and change it to disabled. We can also view the properties of the rule by right clicking it and selecting properties. This will allow you to see what the rule is actually doing, including the ports that are being allowed through the firewall to specific programs.
Creating a rule
Select Inbound Rules from the menu on the left and then select New Rule from the actions pane on the right. This will open the new inbound rule wizard. From here we can select if we want to create a rule for a specific program, to a specific port, or based off of an existing rule.
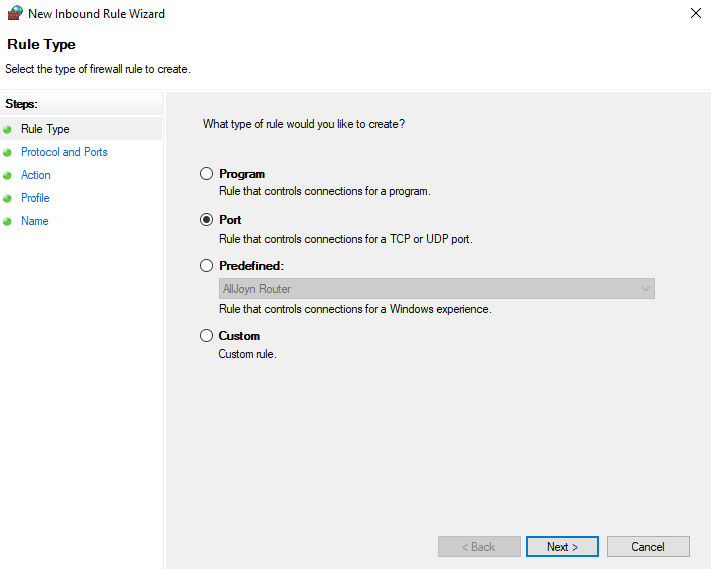
On the next screen we can select the specific program or service that the firewall should allow traffic in for. In this case we’ll just select all programs, however note that this can be used to further lock down a rule, You can create a rule to lock down based on a number of parameters. Make your choices and things based on the requirements for the rule you need to put in place such as ports, IP ranges, programs.